Article: How to control network connections?
Introduction.
In the modern world, almost every computer is connected to some network either permanently or at least from time to time. Networks bring many conveniences, including easy file sharing, remote control, synchronization etc. However, they also bring dangers.
Once you connect your computer to some network, or to the internet, your files are no more secure. Different malware starts probing your defenses. A hacker attack may enable some dangerous features and give other people access to files, folders, or other resources of your computer. Even more dangerous are trojans, keyloggers, viruses. They can be installed with presumably 'free' programs that come from strange places on the internet. Some websites also tend to deceive their visitors by supplying innocent texts to confirmation dialogs, so that the user isn't aware that he or she has been just prompted to install a malware application.
However, all the above listed dangers (and many others) can be eliminated by using a good firewall program. We will take the award-winning Outpost Firewall Pro for our example.
Step 1: Download and install the program.
Download Outpost Firewall Pro to a known location. Run setup and follow on-screen instructions to install the program.
After the installation you will be prompted to set security level. We will use "Normal".
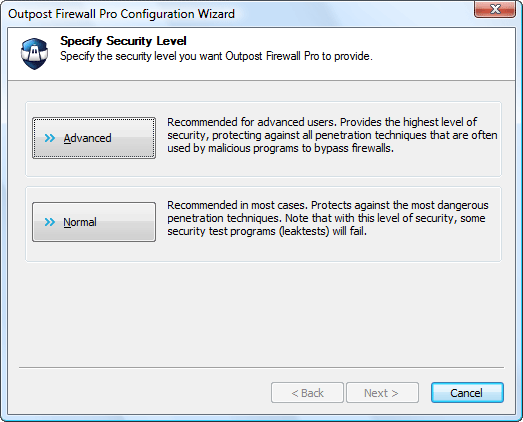
Outpost Firewall Pro also can create rules for applications automatically. This greatly improves security of your computer without bothering you too much.
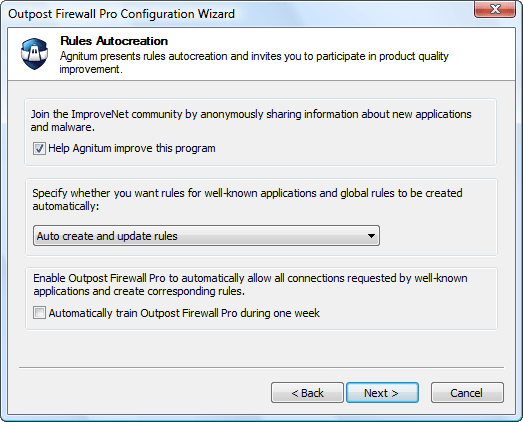
We use defaults here and simply click "Next".
Finally, the program needs to restart our computer in order to enable all its services properly. So, let's do it.
Step 2: Up and running. Control internet connections.
Your computer may take longer to load Windows, as you restart it the very first time after installing Outpost Firewall Pro. This happens because the program runs initial checks and configures its services. It doesn't require much of your attention though. Just let it complete this initial configuration process.
Once up, Outpost Firewall Pro analyzes every connection. Well-known processes are allowed through the firewall automatically, so you don't need to confirm that Internet Explorer on your computer may connect to the internet. But optional applications will need your attention. For example, a popular ICQ client, Miranda, attempts to connect to a remote server:
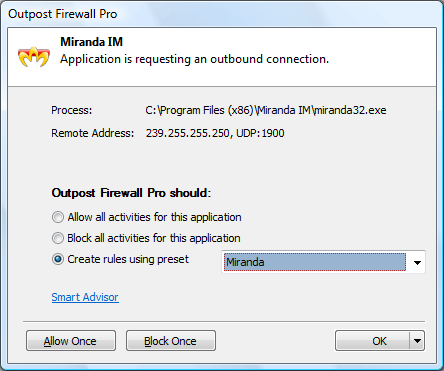
We can immediately create a rule, and we see that there is a preset for Miranda in the database of Outpost Firewall Pro. If we accept the preset, the firewall will allow Miranda doing its usual job.
In such way you can control what programs are trying to make internet connections. If you don't expect some program to connect to the internet, it may be a good idea to review its behavior. Especially if the program has a strange name.
Outpost Firewall Pro is able to detect spyware automatically, so in most cases you get a clear message, if there is a spyware program on your computer. But the firewall will help you block just every program that you don't want to access the internet. By alerting you it also helps you protect your computer from custom made spyware, zero-day malware etc.
The firewall recognizes and blocks all types of hacker attacks. By default it informs the user only in case of a serious threat, but you can set it up to alert you on every single probe from the outside.
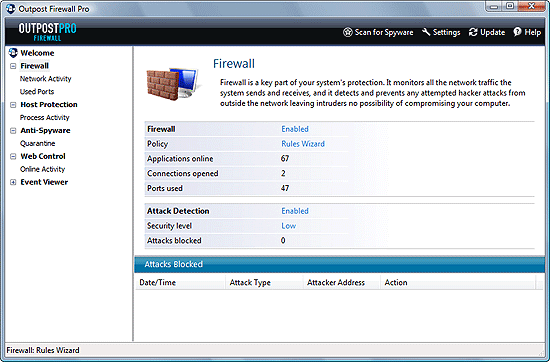
You can see blocked attacks and other information (including the above) if you double-click the tray icon (that with the question mark):
![]()
Outpost Firewall Pro allows you to monitor all network connections and provides detailed information about each of them in real time:
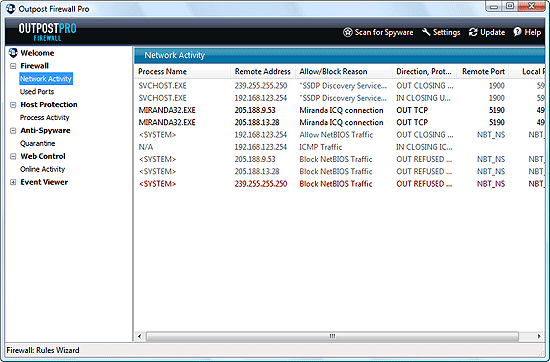
Of course, any rule can be adjusted later. For example, you may decide that some program should be allowed through the firewall, after all. Or, just the opposite, some program shouldn't access the internet.
Outpost Firewall Pro is fully configurable, which means that the user has the most flexible and comprehensive control over network connections. However, it is also intuitive and user-friendly, as its developers constantly work to improve sets of rules for every popular program. Thus you don't actually need to decide which ports should be open and which protocols allowed for a certain application to work properly.
The trial version of Outpost Firewall Pro can be used for free during its evaluation period (30 days).
- Firewall and Intrusion Detection
- Network/Protocol Analyzer
- Network Scanner
- Privacy and Anonymity
- Whois and TraceRoute
- Network Utilities, Suits, Toolkits
- Network Monitor
- Network Traffic Accounting
- Network Inventory
- Remote Control
- File and Disk Encryption
- File and Password Recovery
- Keylogger and AntiKeylogger
- Email Tools
All Categories
Best Recent Downloads
-
PA Server Monitor Ultra
Agentless distributed monitoring of servers and devices
-
GFI WebMonitor - Standalone Proxy Version
Internet monitoring and web security for SMBs
-
GFI LANguard Network Security Scanner
Network vulnerability management solution.
-
Nsauditor Network Security Auditor
Scan and monitor network.Over 45 net tools.
-
10-Strike Network Inventory Explorer
Monitor network computer inventory
-
Network Administrator's Toolkit
Inventory user PCs and monitor servers
-
Net Monitor for Employees
See their screens and take a control.
-
SpotAuditor
Recovers MSN,IE,Outlook,ICQ,Ras,Ftp passwords
-
Alchemy Eye
Server monitoring tool
-
NetResident
Network content monitor
-
Advanced Host Monitor
Award-winning network monitoring software
-
Network Inventory Reporter
inventory software
-
SpotIE Password Recovery
SpotIE recovers Internet Explorer passwords.
-
Asset Tracker for Networks
Inventory network workstations, build reports
-
SpotMSN Password Recover
Recovers MSN messenger and Live passwords.
-
Accent OFFICE Password Recovery
How to break passwords in Office / OpenOffice
-
East-Tec Eraser 2008
Keep what you do on your computer to yourself
-
Security Task Manager
Enhanced Process Viewer that protects your PC
-
NetInfo
A full-featured network toolkit.
-
SpotFTP Password Recover
Recovers FTP passwords stored in computers.
-
Free IP Scanner
A very fast IP scanner and port scanner.

 Product Page
Product Page